- or using a Keycloak setup as your Authentication solution in your native Delphi application.
With no reference to melodramatic intrigues, espionage, secret agents or a Marvel crime-fighting team involving experimental drugs, this post will just try to enlighten how fairly easy it is to get started with Keycloak as an authentication backend for your Delphi application.
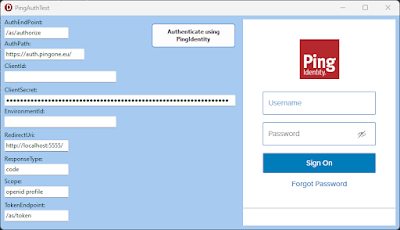
This post is a continuation of some earlier post about IAM related stuff and my Auth component samples for PingOne, EntraID and now Keycloak on GitHub.
The posts can be found here:
Keycloak
Keycloak is a mature Open Source IAM solution, and I am by not means an expert - but I have been dabbling with some of the other provides - and this is as good as any.
The easiest way to get started is to install a docker container as described in the official documentation here.
There are other options and a lot more to it, but that short guide has you started, and we use that sample as the basis for the KeycloakAuth component, found in the last repo link above. Note that at the time of writing this post, it does only parse an access token for the "uniqueid", and the state parameter is by default added.
The state value is a GUID (or should I say UUID) - so to get "proper" UUID, I end up doing this:
begin
FStateValue := TGUID.NewGuid;
URL := URL + '&state=' + GUIDToString(FStateValue).Trim(['{','}']).ToLower;
end;
Using the state parameter in the authorization code flow, helps to check that the client value sent matches the value in the response - to mitigate CSRF/XSRF (Cross-site request forgery) attacks. After that initial check one should then check the nonce given within the id_token.
But getting ahead of myself - to use and play around with my KeycloakAuth component - get it from GitHub as mentioned above - and install the component in the IDE (Delphi 12 package in repo).
As any of my other Auth components, this is based of TWebBrowser - and I hear you ask why not TEdgeBrowser? Well I had done some things similar years back before Edge was a thing, but since I do strongly suggest that the "SelectedEngine" property is set to "EdgeOnly" - TWebBrowser does internally use a TEdgeBrowser. It does mean you do need to install the Edge WebView2 SDK, and deploy the correct dll. Read all about it here.
Create a new VCL application and drop a KeycloakAuth component, align to client and set the following properties:
AuthPath = 'http://localhost:8080/realms/'
ClientId = 'myclient'
RedirectUri = 'http://localhost:1234'
AuthEndpoint = '/protocol/openid-connect/auth'
TokenEndpoint = '/protocol/openid-connect/token'
Scope = 'openid'
UseState = False
ResponseType = 'code'
UserIdClaim = sub
OnAuthenticated = KeycloakAuthenticated
OnDenied = KeycloakDenied
I will add more capabilities to the component - such as nonce and code challenge, and cover all OpenID Connect response_type combinations.
To get a good grasp and overview of the OpenID Connect flows - take a look at this Medium post.
Happy 30th anniversary - Delphi! and see you at Delphi Summit 2025.
/Enjoy